Your cell phone is the key to your mobile identity. From your bank accounts and personal messages, to your social media pages, your phone carries your most sensitive data, and valuable assets. Yet, the protection of this data doesn’t just rely on the security of the phone itself—it depends heavily on the security protocols of the cellular carriers that power your phone’s connectivity.
Unfortunately, traditional mobile carriers have been sleeping on the job, continuing to use outdated authentication methods that leave user accounts vulnerable to attacks. These weaknesses expose customers to account compromise through methods like phishing, brute force, and SIM swap attacks—threats that can lead to unauthorized access to personal data and even financial loss.
At Cape, we understand that the security of your mobile account is just as crucial as the security of the device itself. That’s why we’ve built our service from the ground up with security and privacy as our guiding principles.
Digital Signatures instead of usernames and passwords.
At Cape, we don’t use traditional passwords because we don’t believe they are secure enough to protect your accounts and the sensitive information they hold. Instead, we use modern cryptography to authenticate user accounts through digital signatures.
Digital signatures enhance security by eliminating common vulnerabilities associated with passwords, as well as the general inconvenience of managing and inputting complex passwords at every login. The authentication process with digital signatures is both simpler and more secure, as users prove they possess the private key without ever transmitting the actual key information over the network.
Importantly, Cape’s customer authentication protects against SIM swap attacks. SIM swapping occurs when someone steals your phone number, gaining access to your calls and text messages, including SMS-based two-factor authentication (2FA) codes or one-time passwords. This allows attackers to reset the passwords on your accounts and gain access. SIM swappers often succeed by compromising an insider at your carrier or using stolen information to impersonate you and convince a telco support agent to switch your phone number to a new device controlled by the scammer (read more about how T-Mobile and Verizon employees were offered $300 per hijacked phone line).
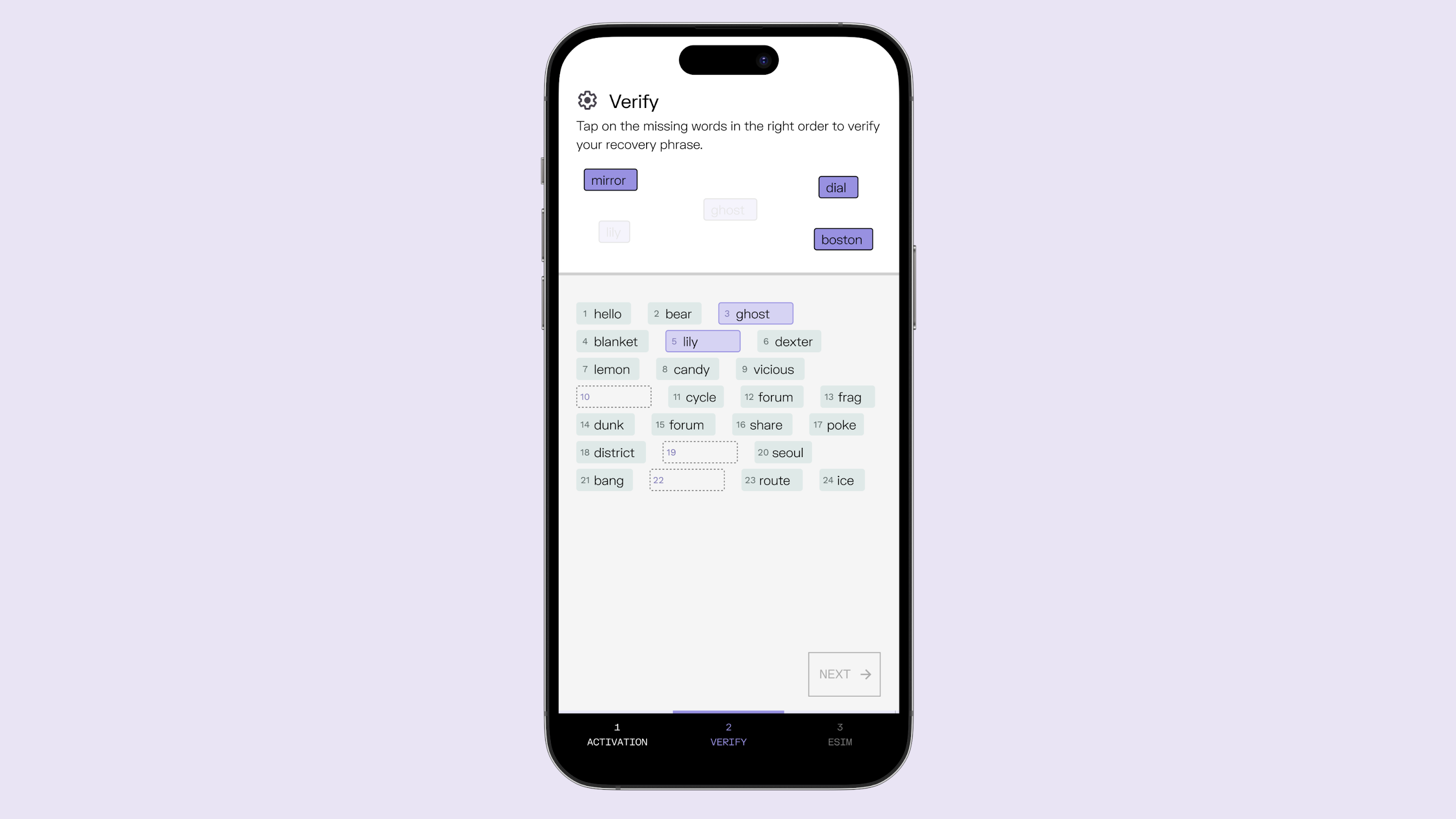
At Cape, we believe that human-in-the-loop procedures for handling sensitive customer requests are inherently less secure. That’s why Cape support agents and employees do not initiate phone number port-outs on your behalf—only you can initiate a port-out, using your own 24-word passphrase.
When you create an account with Cape, you generate a 24-word passphrase on your device instead of a traditional username and password. This passphrase is based on BIP-39 (Bitcoin Improvement Proposal 39), a widely used standard for creating and managing cryptographic wallets in a user-friendly way. The passphrase is generated using specific algorithms that convert random numbers into a list of words selected from a standardized dictionary of 2,048 words.
Cape uses public key cryptography, also known as asymmetric cryptography, to secure your account. Your 24-word passphrase acts as a human-readable representation of a cryptographic seed used to generate your private and public keys.
- Private Key: Kept secret and stored locally and securely on your device. This key never leaves your device, so Cape’s backend, nor any other system, never has access to your private key.
- Public Key: Derived from the private key and used by Cape’s systems to verify your identity.
Whenever you need to access your Cape account or authenticate yourself, such as when replacing your phone or getting a new number, you use your 24-word passphrase. Entering this passphrase regenerates the cryptographic seed, and from that, your private and public keys. Cape’s server verifies your public key with a digital signature based proof of ownership check. Only your on-device private key can generate a valid signature for your public key, ensuring that the person accessing the account is indeed you.
Privacy and Security as Core Principles
Traditional telcos are frequently breached, as seen in the latest AT&T incident, where the communication records of nearly all their customers were exposed. When they’re not losing your data, they’re actively selling it, often securing your consent through obscure opt-ins buried in lengthy privacy policies.
Cape was built with privacy and security as core principles, not as afterthoughts. We believe that your data should belong to you, and that you should have sole control over who accesses it and why.
We’re not just offering another mobile service; we’re offering a reimagined approach to mobile security. Join us in this movement, and switch to Cape today.