There’s a way attackers can track your location, intercept your messages, and compromise your privacy—all without needing any access to your phone and entirely without your knowledge. They don’t need to send you suspicious texts, rely on you to click a phishing link, or install any malware.
If you use a cell phone, you're inherently vulnerable. Even if you follow every best practice—using encrypted messaging apps, avoiding public Wi-Fi, enabling two-factor authentication—your device still relies on telecom networks that weren’t built with security in mind.
The problem isn’t you.
At the heart of this issue is the infrastructure itself. Mobile networks weren’t built with security in mind, but rather for interoperability and seamless global connectivity. When telecom infrastructure was first developed, security was an afterthought—priority was given to ensuring that calls, messages, and data could travel across different networks worldwide. This foundational design choice led to the widespread adoption of SS7 (Signaling System No. 7) and Diameter, two core protocols that allow carriers to exchange information about subscribers, authenticate devices, and route communications across international networks.
However, these protocols were designed for a world where trust between telecom operators was assumed. SS7, which dates back to the 1970s, was built in an era when only a handful of regulated entities had access to telecom infrastructure. Diameter, its modern successor for 4G and 5G networks, was intended to improve on SS7, but still operates within a fundamentally trust-based system. Both protocols allow carriers to verify a subscriber's location, process billing, and enable roaming between networks—but they also lack robust authentication mechanisms, making them an attractive target for attackers.
Because these protocols assume trust, attackers—whether rogue telecom insiders, cybercriminals, or nation-state adversaries—can abuse them to:
- Track a user’s location in real-time by requesting location updates from their home network.
- Intercept calls and messages by redirecting them through attacker-controlled systems.
- Extract unique identifiers (IMSI) from devices to target in further attacks.
While major telecoms rely on outdated signaling firewalls that are easily bypassed, Cape has built an entirely new approach to signaling attack protection—one that removes blind trust from the equation and gives users visibility and control over their network security.
The Growing Threat of Signaling Attacks
Millions of signaling attacks occur every month. Massive amounts of cyber espionage have taken place via signaling pathways for years, and continue to every day. These exploits have been widely documented:
- Congressman Ted Lieu’s phone was hacked on live TV using an SS7 attack, as demonstrated on 60 Minutes Australia.
- Cybersecurity officials have warned the FCC that SS7/Diameter attacks remain an unsolved and active threat.
- A viral Veritasium video showed how a well-known tech influencer’s calls were redirected through an SS7 exploit.
Despite the growing awareness of these risks, telcos rely on signaling firewalls that mainly use “velocity checks” to block improbable location updates.
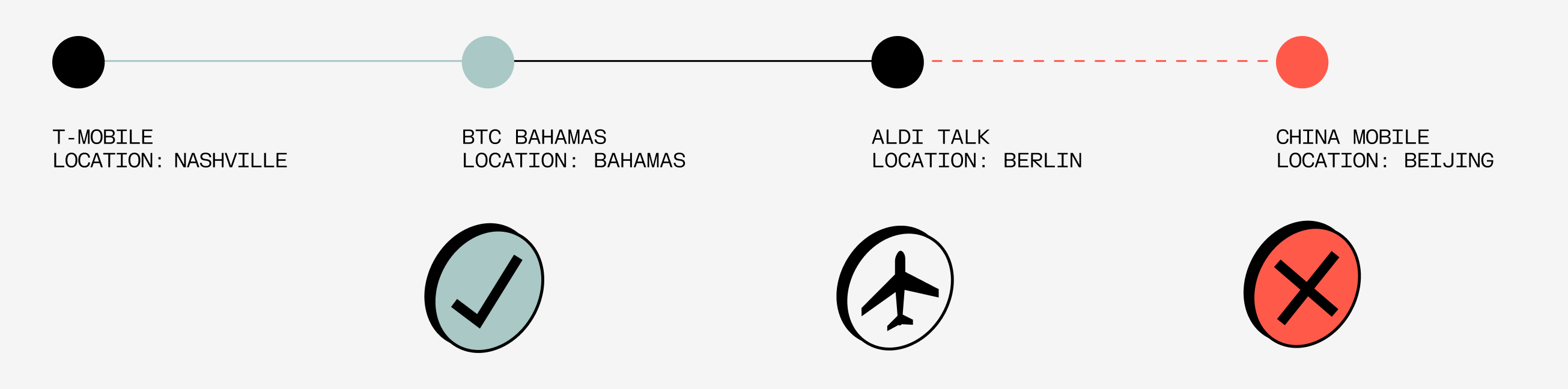
For example, imagine Taylor Swift boards her jet in Nashville, switches off her phone, and begins a flight to Berlin. A malicious actor, posing as China Mobile, could send a message to Taylor Swift’s home carrier T-Mobile, requesting to begin routing all her calls and SMS to China Mobile, effectively claiming that she has shown up on their network and is requesting to roam there.
A velocity check firewall would understand that TSwift switched off her phone in Nashville just a few hours ago and so it’s impossible that she is already roaming on China Mobile’s network. The request to update her location would be rejected, as you can see by the red X.
However, as velocity checks became pervasive, adversary tactics evolved. If an attacker gains access to a nearby carrier—say in Mexico or the Bahamas—they can reroute a target’s phone traffic without raising suspicion. During Taylor’s actual flight to Berlin, T-Mobile could be fooled into thinking that she actually landed in Nassau, and began routing all her calls and SMS to BTC Bahamas.
And now, these attacks are no longer just a tool for governments. Cheap and accessible hacking tools mean even independent bad actors can carry out signaling attacks from anywhere in the world.
Introducing Cape’s Enhanced Signaling Protection: A Different Approach to Signaling Security
At Cape, we’ve taken a fundamentally different approach to stopping signaling attacks. Unlike traditional carriers that rely on outdated defenses, we’ve eliminated direct SS7 dependencies from our network and built a proprietary signaling proxy to handle requests securely.
Here’s how it works:
When a network requests a location update or attempts to attach your phone to a new network, Cape doesn’t just blindly accept the request. Instead, our Enhanced Signaling Protection checks whether the request aligns with your actual location by querying your device directly through the Cape app.
- If the attach request matches your real location: The request is processed normally, and your phone connects as expected.
- If the attach request comes from a suspicious location: For example, if an attacker in another country tries to attach your IMSI to their network, but your device is still in your home city, the request is automatically denied, and you’ll be notified immediately.
Critically, Cape never collects or stores your precise location. Your device performs the location check locally—Cape’s systems simply verify whether the network’s claim matches what your device reports.
This approach ensures that suspicious attach attempts are stopped before they can connect, and your precise location remains private—Cape never sees it.
Signaling Attacks Are Evolving. So Are We.
Traditional carriers have accepted signaling vulnerabilities as an unavoidable risk. We haven’t. Cape’s Enhanced Signaling Protection is built from the ground up for a world where mobile security can’t be an afterthought.
Want to stay ahead of these threats? Join Cape today and experience the future of mobile security.